Installing OSSEC with Splunk allows a better overview of the thousand information collected by the system useful to create reports for the management.
Splunk is the tools that can be integrated into OSSEC to transform the logs in a graphic format with some built-in reports that allows to better check monitored systems.
Configure OSSEC
OSSEC installation procedure can be found in this post.
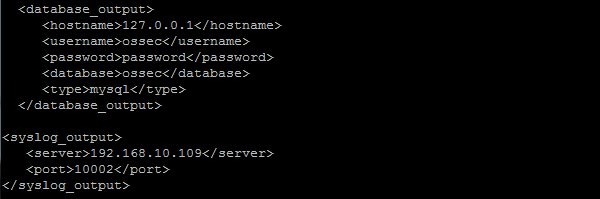
To enable syslog, edit OSSEC configuration file ossec.conf and add the following lines:
<syslog_output> <server>192.168.10.109</server> # OSSEC server IP <port>10002</port> </syslog_output>
# vi /var/ossec/etc/ossec.conf
Enable module syslog_output and restart OSSEC.
# /var/ossec/bin/ossec-control enable client-syslog
# /var/ossec/bin/ossec-control restart
Install Splunk
Download from website latest Splunk release and install the application through rpm command.
# rpm -Uvh splunk-5.0.2-149561-linux-2.6-x86_64.rpm
Edit the configuration file inputs.conf and add this stanza:
[udp://192.168.10.109:10002] # OSSEC server IP disabled = false sourcetype = ossec
# vi /opt/splunk/etc/system/default/inputs.conf
Restart Splunk. If this is the first time application starts, you need to accept the EULA.
# /opt/splunk/bin/splunk restart
Type on your browser http://OSSEC_IP:8000 and login to Splunk using default credential admin/changeme. At first logon, you are prompted to change the password. If the firewall is turned on, add exception TCP:8000.
Splunk main screen.
Install Splunk for OSSEC
Download Splunk for OSSEC application and from Splunk main window click on menu App > Manage apps.
Click on Install app from file button.
Click on Choose File button and select the downloaded file ossec-1.1.89.tgz. Click Upload to load the application into Splunk.
When the application has been uploaded, system needs to be restarted. Click Restart Splunk to continue.
System is then restarted.
Once logged in again into system, you get the notification of installed app.
Clicking Apps on main screen, a list with all installed apps appears. Identify the line Splunk for OSSEC and click Launch app under Actions.
Splunk for OSSEC main screen opens.
Click Dashboards & Views menu and select OSSEC Dashboard option.
Collected data are displayed in graphic format easy to be read at first sight.
Splunk is a powerful tool to display collected data and reports can be easily created selecting available templates under Searches & Reports menu.
Remove data from indexes
To delete indexed data permanently from your disk, from the console run the the following commands:
# service splunk stop
# /opt/splunk/bin
# ./splunk clean eventdata
# service splunk start
This command completely deletes the data in all indexes releasing unused disk space.