
Setting up OSSEC with mySQL and AnaLogi allows to perform log analysis, file integrity checking, policy monitoring and rootkit detection. OSSEC is an open source host-based intrusion detection system.
Running on different systems (Windows, Linux, MAC, …), collected data can be stored in a mySQL database and some reports can be displayed using the web gui AnaLogi.
Prerequisites
Starting from the CentOS 6.4 minimal installation, this procedure relies on three main packages:
- mySQL v5.x database
- OSSEC v2.7 log analyzer
- AnaLogi v1.3 ossec-wui
Install mySQL
Update the system and install mySQL packages and compilers.
# yum update
# yum install mysql-devel mysql-server gcc make
To work properly, SELINUX must be disabled.
# vi /etc/selinux/config
Enable mySQL to start during system boot and start the service.
# chkconfig mysqld on
# service mysqld start
Secure mySQL running the following command.
# /usr/bin/mysql_secure_installation
Install Ossec and create mySQL db
Using the command wget, download the OSSEC package and decompress the file.
# wget http://www.ossec.net/files/ossec-hids-2.7.tar.gz
# tar -vxzf ossec-hids-2.7.tar.gz
Because by default is disabled, enable mySQL in OSSEC.
# cd ossec-hids-2.7/src
# make setdb
Create a new mySQL database to save OSSEC alerts.
# mysql -u root -p
mysql> create database ossec;
mysql> grant INSERT,SELECT,UPDATE,CREATE,DELETE,EXECUTE on ossec.* to ossec@localhost;
mysql> set password for ossec@localhost=PASSWORD(‘password’);
mysql> flush privileges;
mysql> quit
Import the schema for the new database from the OSSEC installation directory ossec-hids-2.7/src/os_dbd/.
# cd ossec-hids-2.7/src/os_dbd
# mysql -u root -p ossec < mysql.schema
Now proceed with OSSEC installation executing the file install.sh.
# ./install.sh
Hit the ENTER button to start the configuration process.
After pressing ENTER, system compiles and install OSSEC in the computer.
If everything goes smoothly, the installation finishes without any warning or error.
If OSSEC works behind a firewall, the communication with the agent occurs through port UDP 1454.
It’s now time to set the mySQL parameters in the OSSEC configuration. Edit the file ossec.conf.
# vi /var/ossec/etc/ossec.conf
Add the following lines:
<database_output> <hostname>127.0.0.1</hostname> <username>ossec</username> <password>password</password> <database>ossec</database> <type>mysql</type> </database_output>
Last step, enable mySQL and restart the service.
# /var/ossec/bin/ossec-control enable database
# /var/ossec/bin/ossec-control restart
Install AnaLogi web interface
Because AnaLogi is a web interface for OSSEC that replaced the outdated ossec-wui, we need to install Apache and PHP in our system.
# yum install httpd php php-mysql mod_ssl
Enable Apache to start during system boot and start the service.
# chkconfig httpd on
# service httpd restart
Because AnaLogi is stored using git repository, we need to install the git package to retrieve the files from the website.
# yum install git-core
Once installed git, download the AnaLogi package using git clone command.
# cd /var/www/html
# git clone https://github.com/ECSC/analogi.git
Assign ownership of AnaLogi directory to user apache.
# chown apache:apache analogi -R
Rename the configuration file.
# cd /var/www/html/analogi
# mv db_ossec.php.new db_ossec.php
Edit the db_ossec.php file and amend the SQL parameters to reflect your installation.
# vi db_ossec.php
If you want creating a virtual host, edit the Apache configuration file and add the following lines:
# vi /etc/httpd/conf/httpd.conf
<VirtualHost *:80>
ServerAdmin admin@nolabnoparty.local
DocumentRoot /var/www/html/analogi
ServerName lx6-ossec01.nolabnoparty.local
ErrorLog logs/ossec-err-error_log
CustomLog logs/ossec-access-access_log common
<Directory /var/www/html/analogi>
Allow from all
Options -MultiViews
</Directory>
</VirtualHost>
Restart Apache.
# service httpd restart
Open your browser and type the URL address:
http://ip_address
https://ip_address/analogi
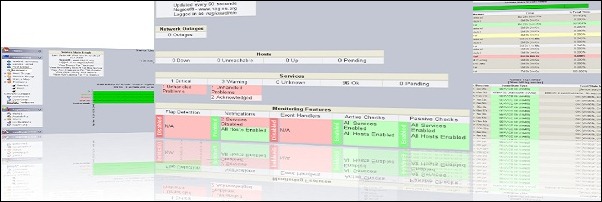
If you can see a similar screen, OSSEC server is working properly.
The OSSEC server is now fully functional, last step to perform is the creation of agents for your clients.
Troubleshooting
During the time data stored in the database make the DB itself quite huge. Two files become quite big: data.MYD and alerts.MYD.
Check the files size with command:
# cd /var/lib/mysql/ossec/
# du * -h
If the size is too big, there are to steps to perform:
- database backup
- tables truncate
Once performed the backup, from the console type the command:
# mysql -u root -p
mysql> show databases;
mysql> use ossec;
mysql> truncate table data;
mysql> truncate table alert;
mysql> quit;
Files size is now smaller.
Delete the integrity history and the alerts.
Stop OSSEC service:
# service ossec stop
Clear the file integrity history:
# /var/ossec/bin/syscheck_update -a
Delete all alerts removing the whole /var/ossec/logs/alerts/* directory:
# rm -rf /var/ossec/logs/alerts/*
Start OSSEC service:
# service ossec start






























My all configurations are correct but it is still showing an error in installation. why so??
Hard to say without any log or additional details.
What error you receive?
Its showing an errorin the last when installing OSSEC from ./install.sh
or from step as you said in this nice post...
"If everything goes smoothly, the installation finishes without any warning or error."
So, should i reinstall ?? or switch to ASL ?? 😐 ..
I installed OSSEC using this guide and he made a mistake on telling where the install.sh file is.
before running ./install.sh you have to do this
1. # cd ossec-hids-2.7
2. # bash install.sh