VMware Horizon True SSO configuration is used to eliminate the credential requests from Active Directory while accessing Horizon virtual desktops and published applications.
After the user login to VMware Horizon with an Identity Provider using UAG, with the True SSO (single sign-on) feature enabled the user is not prompted to enter the Active Directory credentials twice to use VDI or published apps.
UAGs can be configured to leverage SAML capability to enable the communication between Identity Providers (Azure for example) and Horizon using secure tokens with no need to share credentials. This security tokens are SSO certificates generated for each user by the CA and requested by the Horizon Enrollment Server. Bear in mind that SAML doesn't provide any password to Horizon.
Blog series
VMware Horizon True SSO configuration - pt.1
VMware Horizon True SSO configuration - pt.2
VMware Horizon True SSO configuration - pt.3
Firewall ports for Horizon True SSO
The following ports must be open in the Firewall to allow the correct traffic flow.
- TCP 443 - mainly used for the authentication traffic flow.
- TCP 135 - used by the Enrollment Server for the initial communication with the CA then a random port from 1024 – 5000 and 49152 -65535.
- TCP 32111 - used by the Connection Server to use the Enrollment Server.
Install the Enrollment Server
To deploy the True SSO service, a VMware Horizon Enrollment Server must be installed on a Windows machine with at least 4 GB RAM.
The Enrollment Server is used to request a short-lived certificate on behalf of the user that is authenticating against Horizon. This certificate is what True SSO uses to avoid requesting the user to enter the credentials also for Active Directory.
At least one Enrollment Server must be installed to perform True SSO but it is recommended to have two servers for redundancy (active-passive cluster) and it cannot be installed on the same server as the Connection Server. The Enrollment Server can be installed in the same server as the CA and to optimize the performance it should be configured to prefer using the local CA.
To install the Enrollment Server you need a Windows Server VM and the same installer file used for the Connection Server.
Run the installation wizard and click Next.
Accept the EULA and click Next.
Leave default Destination Folder and click Next.
From the drop-down menu select Horizon Enrollment Server option and click Next.
Select Configure Windows Firewall automatically and click Next.
Click Install to proceed with the installation.
The software is being installed.
When the installation has been completed successfully, click Finish to exit the wizard.
Setup a Certification Authority
If a CA is not available in your network, you must install the CA before going ahead with the procedure. The Certificate Authority must be an Enterprise CA type and can be installed on the same server as the Enrollment Server.
Install the CA
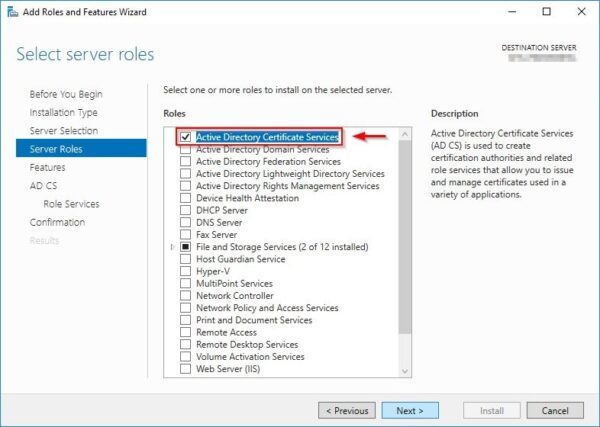
Login to a Windows-based machine and from the Server Manager click the Add roles and features link to install the Certification Authority role. Since the installation procedure is straightforward (just click Next), only the key steps are shown.
Select Active Directory Certificate Services role and click Next.
For True SSO purposes, you only need to select Certification Authority option as Role Services.
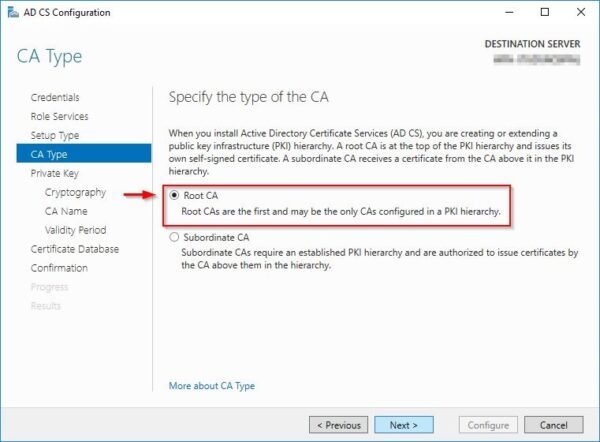
During the configuration wizard procedure, make sure to specify the CA as Enterprise CA.
If you don't have any CA installed in your infrastructure, select Root CA as CA type to install.
Configure CA in the same server
If the CA is installed on the same server as the Enrollment Server, run regedit in the Enrollment Server and navigate to HKLM\Software\VMware, Inc.\VMware VDM. Right click VMware VDM and select New > Key.
For the new key enter the name Enrollment Service. Then right click the new created key and select New > String Value to create a new String (REG_SZ).
Specify PreferLocalCa as key name then right click the created key and select Modify. Enter TRUE in the Value Data field and click OK to save the configuration.
Configure the Certificate Authority
Once the Certification Authority has been installed, open the Command Prompt and run the following command to configure the CA for non-persistent certificate processing.
C:\> certutil -setreg DBFlags +DBFLAGS_ENABLEVOLATILEREQUESTS
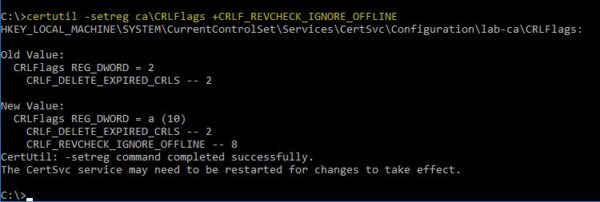
Then run the following command to ignore offline CRL (certificate revocation list) errors on the CA:
C:\> certutil -setreg ca\CRLFlags +CRLF_REVCHECK_IGNORE_OFFLINE
Restart the service.
C:\> sc stop certsvc
C:\> sc start certsvc
Configure the Certificate Template
Open the the Certification Authority and right click the Certificate Templates folder. Select Manage option.
From the list, right click the Smartcard Logon template and select Duplicate Template.
In the duplicated template, configure the following:
Compatibility
- Select Windows Server 2008 R2 from the Certification Authority drop-down menu.
- Click OK to confirm.
- Select Windows 7 / Server 2008 R2 from the Certificate Recipient drop-down menu.
- Click OK to confirm.
General
- Specify a Template display name.
- Set 1 day for the Validity period and 18 hours for the Renewal period.
Request Handling
- Select Signature and smartcard logon in the Purpose field.
- Enable the option For automatic renewal of smart card certificates, use the existing key if a new key cannot be created.
Cryptography
- Select Key Storage Provider as Provider Category.
Server
- Enable the Do not store certificates and requests in the CA database option.
- Uncheck Do not include revocation information in issued certificates option.
Issuance Requirements
- Check the This number of authorized signatures option and enter 1.
- Select Application policy option from the drop-down menu Policy type required in signature.
- Select Certificate Request Agent option from the drop-down menu Application policy.
- Select Valid existing certificate option.
Security
- Click Add button and add the Enrollment Server previously created.
- Select the added Enrollment Server and check Allow option for the Enroll permission.
- Click OK to save the template configuration.
The created certificate template.
Now right click the Enrollment Agent (Computer) template and select Properties.
In the Security tab, add your Enroll Server and check Allow option for the Enroll permission.
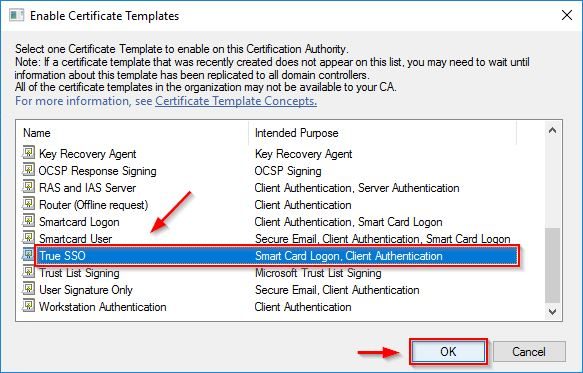
Right-click Certificate Templates and select New > Certificate Template to Issue.
Select the previously created template (True SSO in the example) and click OK.
Right-click Certificate Templates and select New > Certificate Template to Issue once again.
Select the Enrollment Agent (Computer) template and click OK.
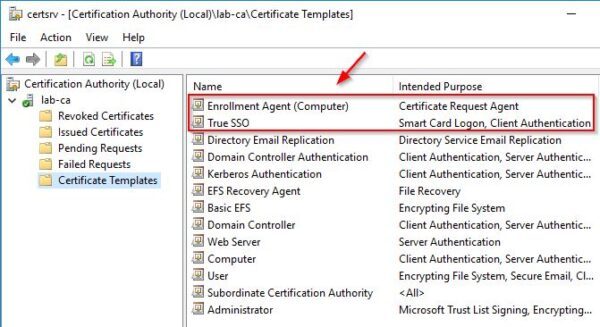
The configured certificate templates. If you have an existing CA in your network and you are configuring a subCA, delete all certificate templates except for the two new created templates.
Install the certificate to the Enrollment Server
Now you need to import the certificate in your Enrollment Server.
Login to the Enrollment Server and from the Run window run the certlm.msc command to open the Certification console. Click OK.
Right click Personal and select All Tasks > Request New Certificate.
Click Next.
Select Active Directory Enrollment Policy (default) and click Next.
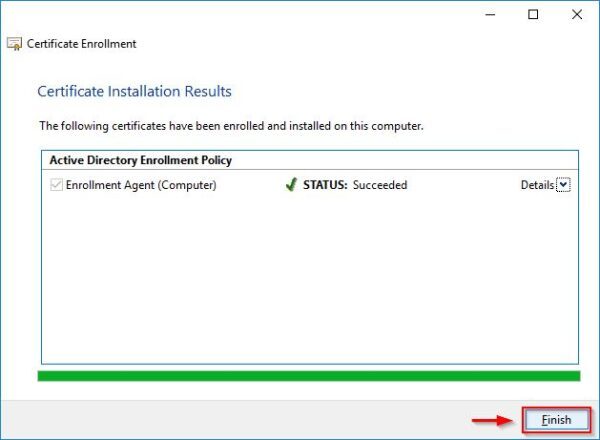
Select Enrollment Agent (Computer) and click Enroll.
Click Finish.
The certificate has been installed successfully.
Part 2 will cover the export/import procedure of the certificate and the configuration of SAML authentication in the UAG.