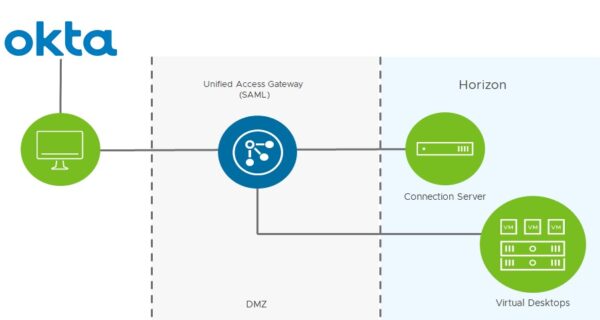
To provide MFA during the authentication process, Okta SAML can be integrated in VMware UAG to increase the security level of your Horizon VDI infrastructure.
SAML (Security Assertion Markup Language) is an XML-based standard for transferring identity data between two parties:
- Identity provider (IdP) - Okta
- Service provider (SP) - UAG
picture from vmware
Blog series
VMware UAG: Okta SAML integration - configure Okta environment
VMware UAG: Okta SAML integration - configure SAML in Okta and UAG
Setup Okta environment
To configure the Okta platform you need to login to the Admin console first.
Using your preferred browser enter the URL https://okta.com and click Login to access the console. Enter your Username and click Next.
Enter the correct Password and click Verify.
Click Admin to begin the Okta environment configuration.
The Okta dashboard.
To leverage MFA capability, Okta needs to be synced with Active Directory to authenticate Users during the login process to your VMware Horizon infrastructure.
Okta SAML Agent prerequisites
Before proceeding with Okta configuration, you need to meet some prerequisites.
To authenticate the users who need to access Horizon VDIs, you need to synchronize your Active Directory with Okta. This requirement is achieved by installing an Okta Agent in an on-prem server.
The used server must meet the following prerequisites:
- The Windows Server can be virtual or physical.
- 2 vCPUs and 8GB RAM.
- The Okta Agent can be installed in Windows 2016/2019/2022.
- The server must be joined to the domain as member. The Host can be a member of any domain in the same forest.
- The .NET 4.6.2 or later must be installed on the server.
- An Okta service account is required to install and run the agent.
Download Okta Agent
From Okta Admin console, go to Directory > Directory Integrations area and click Add Active Directory.
Click Set Up Active Directory.
Click Download Agent.
Once the Agent has been downloaded, you need to install the Agent in your on-prem server to establish the connection to Okta portal using URL and account reported in the Admin console.
Create Active Directory Okta service account
Before proceeding with the Agent installation, you need to create the service account in your Active Directory (okta.service in the example) used to run the Agent service.
Assign the following permissions:
- Add the Okta service account to the Pre-Windows 2000 Compatible Access group.
- Assign the Read all properties for the AD objects to sync.
Make sure to include the Okta service account as member of the local Administrators group in the on-prem server.
Login the on-prem server using the Okta service account and copy the Agent installer. Run the installer and click Next to begin the installation.
Leave default Installation folder and click Install.
A required component is installed in the server.
Specify the correct Domain name and click Next.
If you have already created the service account, select Use an alternate account that I specify option and enter both Username and Password. Click Next.
If this message is displayed, make sure the service account is a member of the Pre-Windows 2000 Compatible Access AD group.
Click Next.
In the Enter Organization URL field enter the URL as indicated in the Okta portal (https://trial-9648815.okta.com in the example). The URL can be customized when a valid license has been purchased. Click Next.
Enter your Username and click Next.
Enter the Password and click Verify.
Click Allow Access to grant requested permissions.
The Agent is being registered.
Click Finish to close the installation wizard.
Open the Okta AD Agent Management Utility and verify if the Agent is running.
Configure AD in Okta portal
Move back to Okta portal. Once the Agent established the connection with Okta portal, click Next.
Select OUs to sync Users and Groups from and leave default Okta username format. Click Next.
Click Next.
Leave default attributes and click Next.
The Agent setup is complete. Click Done.
Import Users and Groups in Okta
From Directory Integrations area, select the Import tab and click Import Now.
Since this is the first import, select Full import and click Import.
The system starts importing Users and Groups from the selected OUs.
After a few seconds, Users and Groups have been imported in Okta. Click OK.
Now select users to assign to Okta and click Confirm Assignments.
Enable Auto-Activate users after confirmation checkbox and click Confirm.
Selected Users have been assigned and confirmed.
The setup of the Directory integration is now complete and Okta can now synchronize the configured OUs.
Part 2 will cover the SAML configuration in Okta and UAG with a connection test to verify if everything works as expected.

















































